/ What Is Cloud Encryption?
What Is Cloud Encryption?
Cloud encryption is a data security process in which plaintext data is encoded into unreadable ciphertext to help keep it secure in or between cloud environments. It is one of the most effective ways to uphold data privacy as well as protect cloud data in transit or at rest against cyberattacks. Anywhere, anytime access to apps and data is a key advantage of the cloud, but such ubiquitous access—often to sensitive data—requires strong data protection, of which cloud encryption is a crucial part.
How Does Cloud Encryption Work?
Cloud encryption protects sensitive information as it traverses the internet or rests in the cloud. Encryption algorithms can transform data of any type into an encoded format that requires a decryption key to decipher. This way, even if an attacker intercepts or exfiltrates the data, it’s useless to them unless they can decrypt it.
Cloud encryption protects data in two basic states:
- Data in transit between destinations, often outside a secure network, making it more vulnerable.
- Data at rest in cloud storage, a data center server, or similar, and not being used or moved.
Today, standard HTTPS web traffic encryption uses Transport Layer Security (TLS; aka SSL) protocol to secure each data packet. When trusted users or entities (established through multifactor authentication) request access to encrypted data, they receive it in its encrypted state and must use a decryption key to render it usable.
Two Basic Types of Data Encryption
All cloud encryption services and protocols fall into two main categories: symmetric and asymmetric encryption.
Symmetric Encryption
In symmetric encryption, a single key is used to encrypt plaintext and decrypt ciphertext. As a simple example, if you encoded the word “cat” by moving each letter four characters ahead in the alphabet—to ”gex”—you could do the opposite to decode it back to “cat” again.
Symmetric protocols like the Advanced Encryption Standard (AES) and TLS (which can also be asymmetric; more on that below) are used today because they’re:
- Complex enough to be secure—cracking AES with brute force could take billions of years
- Simple enough to be fast—well suited to dealing with large data sets and volumes of traffic
However, this single-key approach is more easily compromised. For instance, if an encryption key needed to be sent over the internet, an attacker could intercept it and expose the encoded data.
Asymmetric Encryption
In asymmetric encryption, encoding and decoding are done with linked public and private key pairs. This is like a coded padlock: you can lock it (using a public key) without knowing the code, but only the person who knows the code (the private key) can open it again.
Asymmetric approaches like elliptic-curve cryptography (ECC), the Digital Signature Algorithm (DSA), and TLS are used today because they’re:
- Less vulnerable to compromise—exposed public keys can’t expose private keys, and private keys never need to be transmitted
- Another form of authentication—a sender can sign a file with a private key to prove its origin to the recipient
Compared to symmetric encryption, the biggest downside to asymmetric encryption is that, broadly speaking, it tends to be slower.
Benefits of Cloud Encryption
Whatever form it takes, the core advantages of any cloud encryption center on:
- Better cybersecurity: Protect data against compromise wherever it is, in motion or at rest, in the cloud or with an end user.
- Tighter compliance: Meet the encryption requirements of regulatory standards such as HIPAA, PCI DSS, and FIPS.
- Lower risk: Some data breaches may not need to be disclosed if all data involved in the breach was encrypted.
- Stronger trust and privacy: Reinforce trust in your organization, brand, or product by emphasizing privacy in data handling, bolstered by effective encryption.

According to the Google Transparency Report, as of January 2024, 96% of pages in Chrome in the US are loaded over HTTPS.
When Do You Need Cloud Encryption?
What to encrypt, and when, depends on the nature and security needs of the data. For instance, the Health Insurance Portability and Accountability Act (HIPAA) and Payment Card Industry Data Security Standard (PCI DSS) govern how healthcare organizations and entities that process credit/debit transactions, respectively, must handle data encryption to avoid fines or legal consequences. There are also many government regulations worldwide, such as the Federal Information Processing Standards (FIPS) in the US.
Compliance frameworks exist to reduce the risk of data breaches, but a simple truth can’t be ignored: the breaches continue. This is in part because different cloud deployments and cloud providers are subject to different regulations, uphold different policies, and have different vulnerabilities. In short, to maintain strong cloud security, it’s best to encrypt as much data as possible, whenever possible, whatever the specific security requirements of the data.
Real-World Example: Equifax Breach
The 2018 breach of credit reporting firm Equifax exposed the personally identifiable information (PII) of more than 148 million people. Proper encryption and inspection practices would have made this far less likely.
The breach went undetected for 10 months because an expired site certificate let encrypted traffic pass uninspected, enabling the attacker to exfiltrate customer data over an encrypted connection without being detected. In addition, had the data been encrypted before it was uploaded, the attackers would have only exposed unreadable ciphertext.
Why Inspecting Encrypted Traffic Matters, Too
Secure encryption is crucial, but without inspection, it just creates blind spots.
According to the Google Transparency Report, worldwide, more than 90% of traffic to Google is encrypted. This keeps sensitive data safe, but it can also help attacks hide. Zscaler research has found that more than 80% of attacks now happen over encrypted channels.
More Easily (and More Often) Said Than Done
Despite the risk, most organizations don't decrypt and inspect most of their encrypted traffic, leaving themselves vulnerable. The “why” of it comes down to a few things:
- Full inspection takes a huge amount of processing power. The explosive popularity of cloud computing means there’s more traffic on the internet than ever, compounding the issue further. Many organizations are using legacy security hardware that doesn’t have the capacity to offer performance and security at the same time.
- Some organizations don’t inspect “trusted” traffic. Service providers like Google, Microsoft, and AWS maintain their own information security controls, which many organizations take to be sufficient protection. Attackers know this, which makes traffic from these providers a popular way to sneak into a target environment.
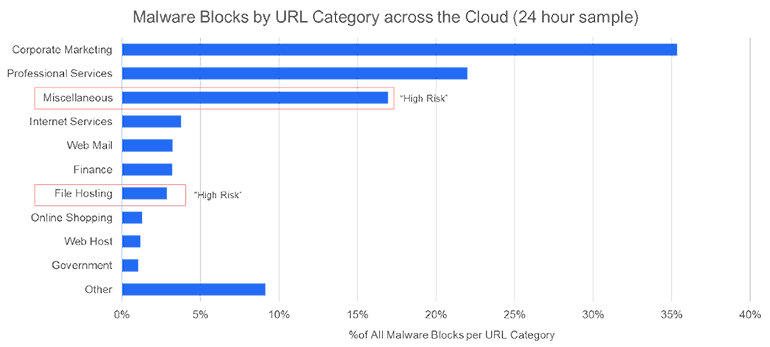
- Some legacy vendors call targeted decryption a best practice. Related to both of the above, vendors of capacity-limited firewall hardware often publish deployment “best practices” that recommend only decrypting traffic in “high risk” URL categories, while trusting the rest. Take a look at the chart here to see what that could mean.
Read SSL Inspection Comes with Great Responsibility to learn more.
Cloud Encryption and Inspection in Today’s Landscape
Let’s look at this from ground level. The volume of web traffic has shot upward in the last few years, and organizations that haven’t upgraded or replaced their on-premises security solutions are facing more attacks, dealing with far slower SaaS and general cloud performance, or likely both.
At the same time, there’s been an explosion in reliance on cloud storage providers and cloud services, of which there are many different types with different balances of security responsibility.
And finally, alongside many new cloud providers and services, older providers are working to keep the lights on, offering recommendations on how you can stay safe enough as you continue to use their solutions for use cases they weren’t built to address.
The problem lies in that idea of being “safe enough.” With attacks on the rise, “as safe as possible” is a better way forward. To truly minimize risk and reduce costs, your inspection solution needs to be capable of scaling to decrypt, inspect, and re-encrypt all traffic, whatever its source, without slowing down your operations—otherwise, at best, it just shifts costs around. And at worst, you’re anything but “safe enough.”
Zscaler and Cloud Encryption
Zscaler Internet Access™ (ZIA™), part of the Zscaler Zero Trust Exchange™ platform, delivers full inspection at cloud scale—including encrypted traffic—without degrading performance. A fully cloud native service, the platform leverages an advanced cloud proxy architecture to decrypt, inspect, and re-encrypt 100% of traffic to or from any destination or user, protecting your users and your entire organization from threats hiding in encrypted channels.





